In partnership with leading technology vendors, we offer the best of breed security & networking solutions

A10 Networks
A10 Networks Application Delivery Controllers (ADC), Carrier-Grade NAT (CGN), and DDoS Protection
www.a10networks.com
www.a10networks.com

Allot Communications
Bandwidth Management, and Broadband Traffic Management Solution
www.allot.com
www.allot.com

Arbor Networks
DDoS Mitigation, Network Visibility, and Advanced Threat Protection
www.arbornetworks.com
www.arbornetworks.com

Check Point
Next-Gen Firewall, APTs Solution, and Endpoint Security
www.checkpoint.com
www.checkpoint.com

CyberArk
Privileged Account Security Password Management, and Session Recording
www.cyberark.com
www.cyberark.com

FireEye
APTs protection for Web, Mail, Mobile, and Endpoint
www.fireeye.com
www.fireeye.com

ForcePoint
Web, Mail Security, DLP and Next-Gen Firewall
www.forcepoint.com
www.forcepoint.com
Infoblox
DNS, DHCP, and IP Address Management (IPAM)
www.infoblox.com
www.infoblox.com

Gemalto
2 Factor Authentication, Data Encryption, HSM
www.gemalto.com
www.gemalto.com

Micro Focus
ArcSight, Fortify (SIEM, Web App Security
www.microfocus.com
www.microfocus.com

PulseSecure
SSLVPN, NAC, and BYOD
www.pulsesecure.com
www.pulsesecure.com

Rapid7
Vulnerability Assessment, Penetration Testing, and Web Application Scan
www.rapid7.com
www.rapid7.com

Ruckus
Wireless solution, BYoD
www.ruckuswireless.com
www.ruckuswireless.com

SilverPeak
Software-defined WAN, WAN/SaaS Optimization, and Replication Acceleration
www.silver-peak.com
www.silver-peak.com

Skybox Security
Security Policy Management, Vulnerability & Threat Management
www.skyboxsecurity.com
www.skyboxsecurity.com

TrendMicro
TippingPoint Network Security Solutions (TPS, NGIPS, and ATP)
www.trendmicro.com
www.trendmicro.com
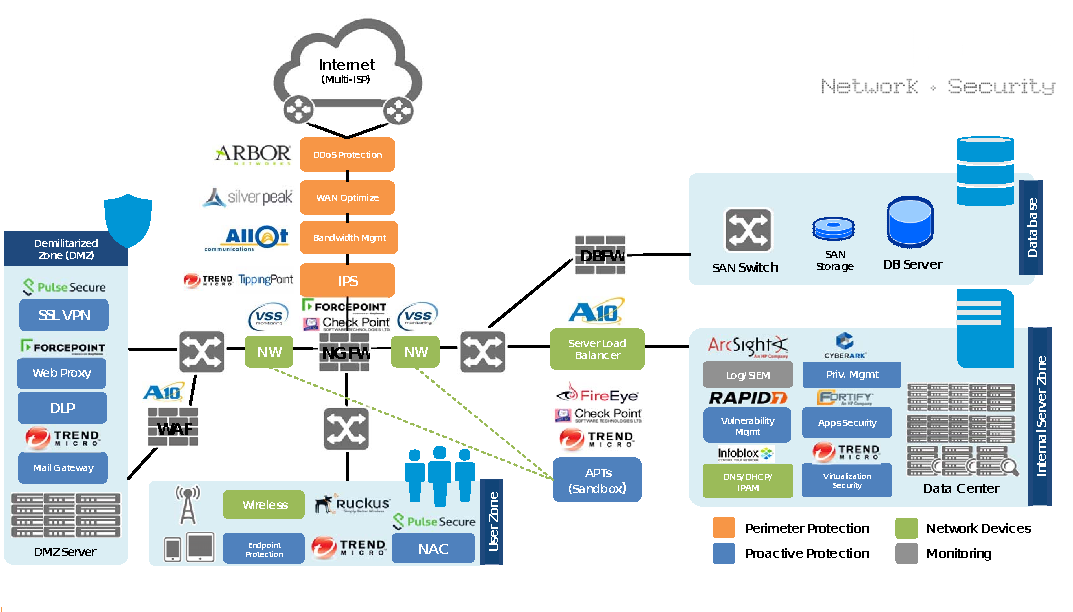
Network Security Blueprint for Enterprise